In our last post, we busted some backup myths, talked about ransomware resilience and showed how MSPs can become true business continuity partners. Now, we’re back with a fire drill for ransomware. Let’s see what to do when your clients are already under attack and how a solid backup and recovery strategy can pull them out of the fire.
Why backup and recovery is your first line of defense
Ransomware recovery is a business survival moment. Downtime from an attack impacts everything from client trust and compliance to insurance coverage and, in some cases, the solvency of the business itself. When ransomware hits, your client’s ability to recover quickly and cleanly is what separates a minor disruption from a full-blown disaster.
It all starts with the right foundation
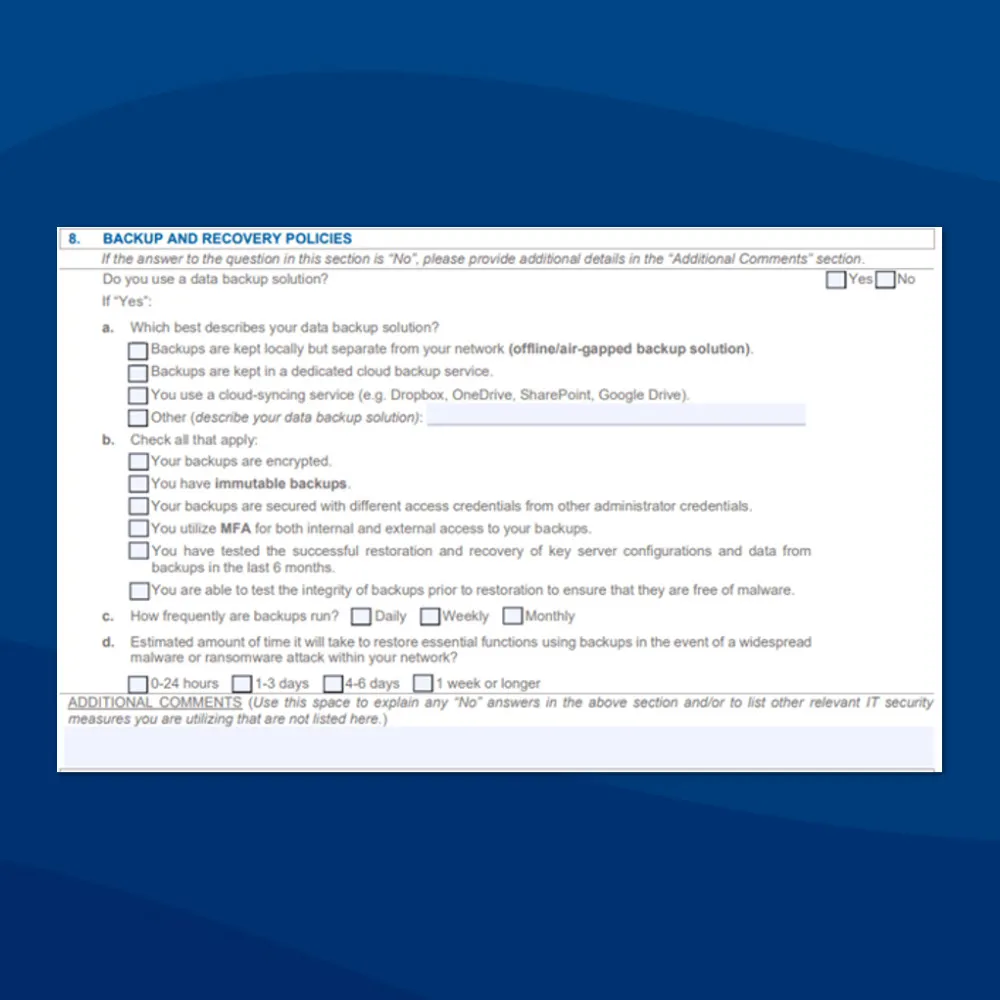
Backups alone won’t save your clients. However, they are the foundation of every effective recovery. For MSPs, that means adopting a strategy built on proven architecture like Datto’s.
- Immutable storage that protects backups from being altered by ransomware.
- Frequent, verified backups that ensure minimal data loss.
- Off-site replication that offers resilience even in the case of site-wide outages.
- Cloud virtualization and sandbox testing that provide clean recovery environments away from infected infrastructure.
- Integrated ransomware detection that automatically flags abnormal behavior before you restore corrupted data.
Restoring one virtual machine (VM) is one thing, but when ransomware hits hundreds of systems, you need orchestration and control — and that starts with a robust backup and recovery strategy.
Before your recovery: The immediate response that matters
Rushing into recovery can do more harm than good. Before restoring systems, MSPs need to follow a clear response protocol to contain the threat and ensure a clean path forward.
Contain first, then investigate
Start by isolating infected systems from the network to prevent lateral spread. Loop in your full security stack — endpoint detection and response (EDR), security information and event management (SIEM) and security operations center (SOC) — to determine how the breach occurred and whether data was exfiltrated, especially in suspected double extortion attacks.
If sensitive data is involved, immediately notify law enforcement, engage legal counsel and contact your cyber insurance provider to stay compliant with policy obligations.
Validate before you restore
Recovery only works if the environment is clean. Confirm that malware has been fully eradicated from production systems and that the root cause has been addressed. Then, verify that your chosen restore points are intact and malware-free — some insurers may even require third-party tools to validate this.
During your recovery: 5 steps that define a successful restoration
Once the threat is contained and your environment is validated, recovery can begin. Here are the five critical steps to ensure a clean and successful restore:
1. Identify the last clean backup
Use anomaly detection logs, ransomware detection alerts, retention policies and application verification to locate a restore point before the infection occurred.
2. Isolate and test before restoring to production
- Restore into a sandboxed, isolated environment.
- Run antivirus and anti-malware scans — note that cyber insurers may require specific tools for compliance.
- Before proceeding, validate key systems for integrity, such as enterprise resource planning (ERP), customer relationship management (CRM) and file shares.
3. Plan phased production restoration
- Map dependencies between machines and services.
- Prioritize mission-critical systems to restore business operations quickly.
- Monitor restored systems closely for any abnormal behavior.
4. Communicate with clients and leadership
- Set clear expectations and be transparent on recovery time objectives (RTOs).
- Keep detailed documentation — insurers may request a step-by-step record of your recovery process.
5. Follow post-restore hygiene
- Reset credentials, especially for administrative accounts.
- Apply pending patches, especially to systems that may have been the attack vector.
- Re-engage users with updated security training to prevent future incidents.
Cyber insurance considerations: What MSPs need to know
Cyber insurance providers are tightening their standards and MSPs need to be ready. Most cyber insurance policies require:
- Documented incident response plans, including disaster recovery (DR) runbooks, automated workflows, dependency maps and network configurations.
- Immutable, off-site and regularly tested backups that stand up to ransomware threats.
- Proof of strong cyber hygiene and regular end-user awareness training.
Your recovery process can also affect claim outcomes. If your recovery takes 21 days but your policy only covers seven, you risk partial or even full denial.
After your recovery: Strengthening your future resilience
The goal isn’t just to recover; it’s to be better prepared for what’s next.
- Run a full post-incident review
Conduct a detailed postmortem to identify what went wrong and how to improve. Adjust retention periods, backup frequency or architecture as needed — especially to outlast sleeper ransomware.
- Reinforce user awareness and training
Renew client security training and run tabletop recovery exercises to reinforce safe behavior and to keep you aligned with compliance and insurance expectations.
- Position yourself as a continuity partner with strategic questions
“When was the last time we tested DR with a full or partial failover?”
“How many days could your business realistically afford to be offline?”
“Should we review your cyber insurance policy to confirm you meet the requirements?”
Be a continuity partner, not just a responder
MSPs who guide clients through proactive planning, routine testing and resilient recovery can become strategic partners in an era where downtime can define a business’s fate. Struggling to show clients just how critical business continuity really is? Try the Recovery Time & Downtime Cost Calculator to reveal the real financial impact and turn awareness into action.
Ready to lead with confidence and deliver real business continuity? Become a Datto Partner.








